How to enable auto-forwarding in Exchange

Introduction
Recently I had the need to enable auto-forwarding for one user account and I figured it would be a perfect subject for another post. It is very important to gain control over forwarding, as this can be the most dangerous method in data exfiltration. Users can easily configure auto-forwarding to some personal email addresses, which later get hacked and your organisation then faces the consequences, so be careful how much forwarding you allow. Generally this article will be about allowing forwarding, but you can use the same paths to block it.
Types of Auto-Forwarding
There are multiple ways a user can achieve auto-forwarding.
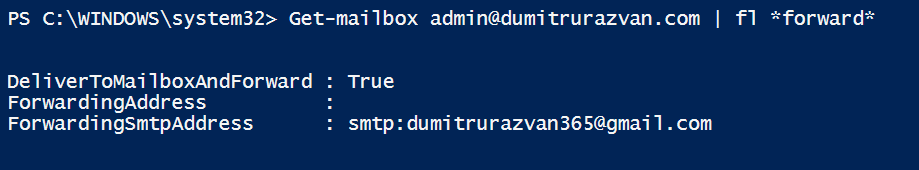
- Forwarding Address - is regularly used for internal forwarding and can only be configured by an admin:
Set-Mailbox -Identity "userA@domain.com" -ForwardingAddress "userB@domain.com" -DeliverToMailboxAndForward $True- note the last parameter which can be $True or $False - Forwarding SMTP Address - can be easily set up by the user (from GUI: Outlook or OWA for example. Alternatively an admin can configure it from the mail tab, on the user, from admin.microsoft.com -> users)
- Inbox Rule - Can be configured by the user via Outlook or OWA.It represents this rule that will evaluate and process each message. You can also see/configure Inbox Rules from Powershell as an admin.
How To Block/Unblock Forwarding at O365 Level
Other than the Powershell options you have at user level (from the previous chapter), you also have a few places where you can configure or block auto-replies or auto-forwarding emails:
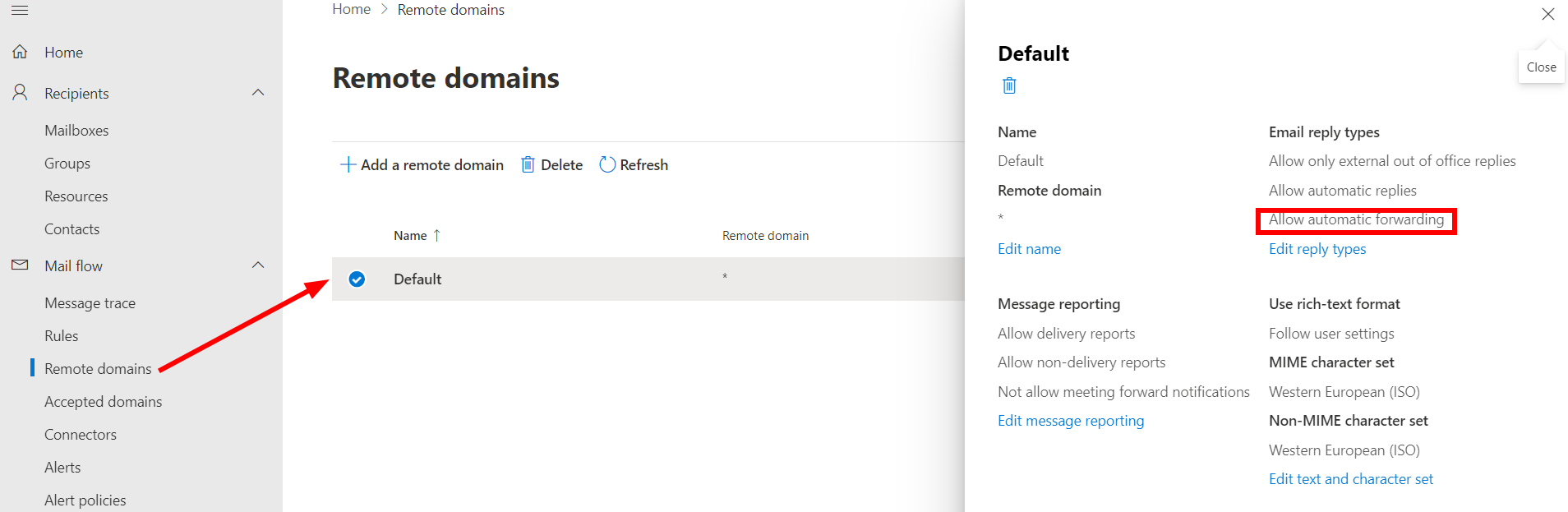
- Remote Domains:
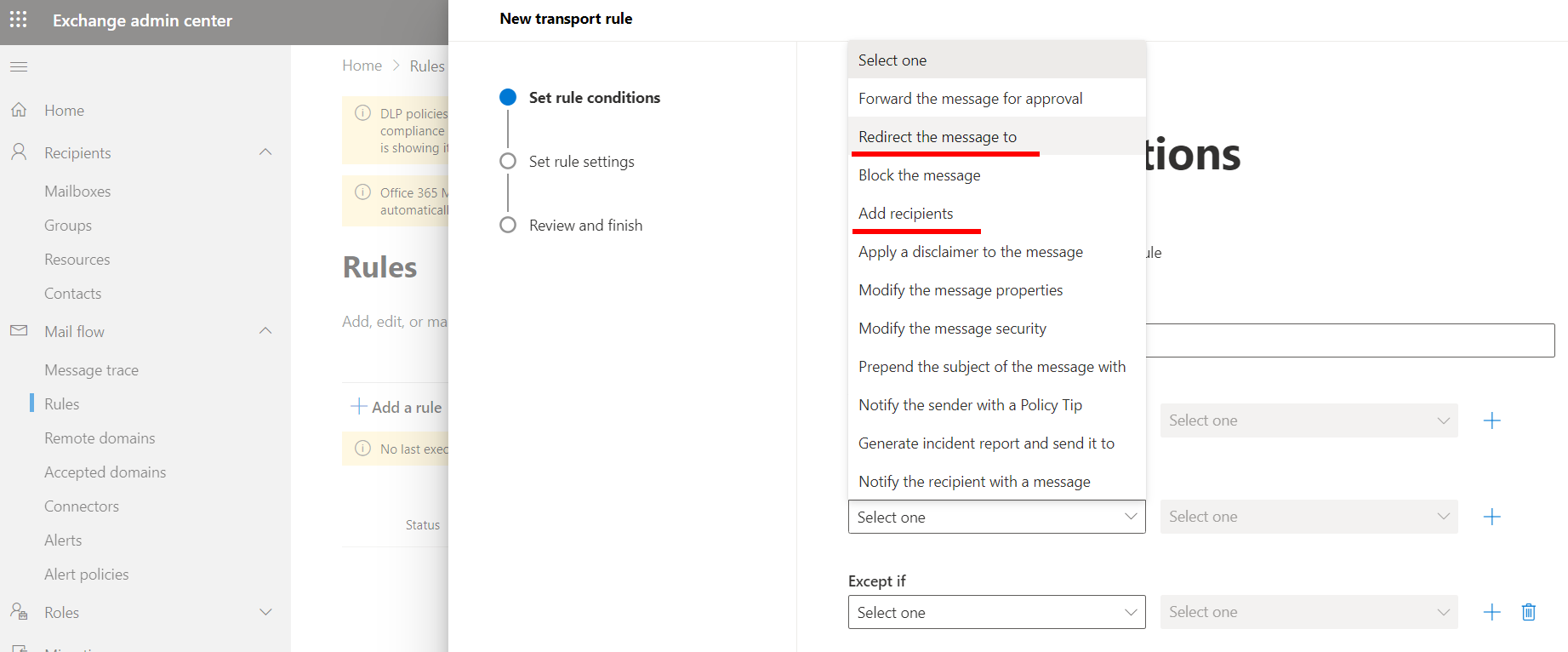
- Exchange Transport Rules (a bit overkill in my opinion, but you can find some options here):
- Anti-Spam Policy: This one is a bit tricky, you will have to go on the Security.Microsoft.com portal
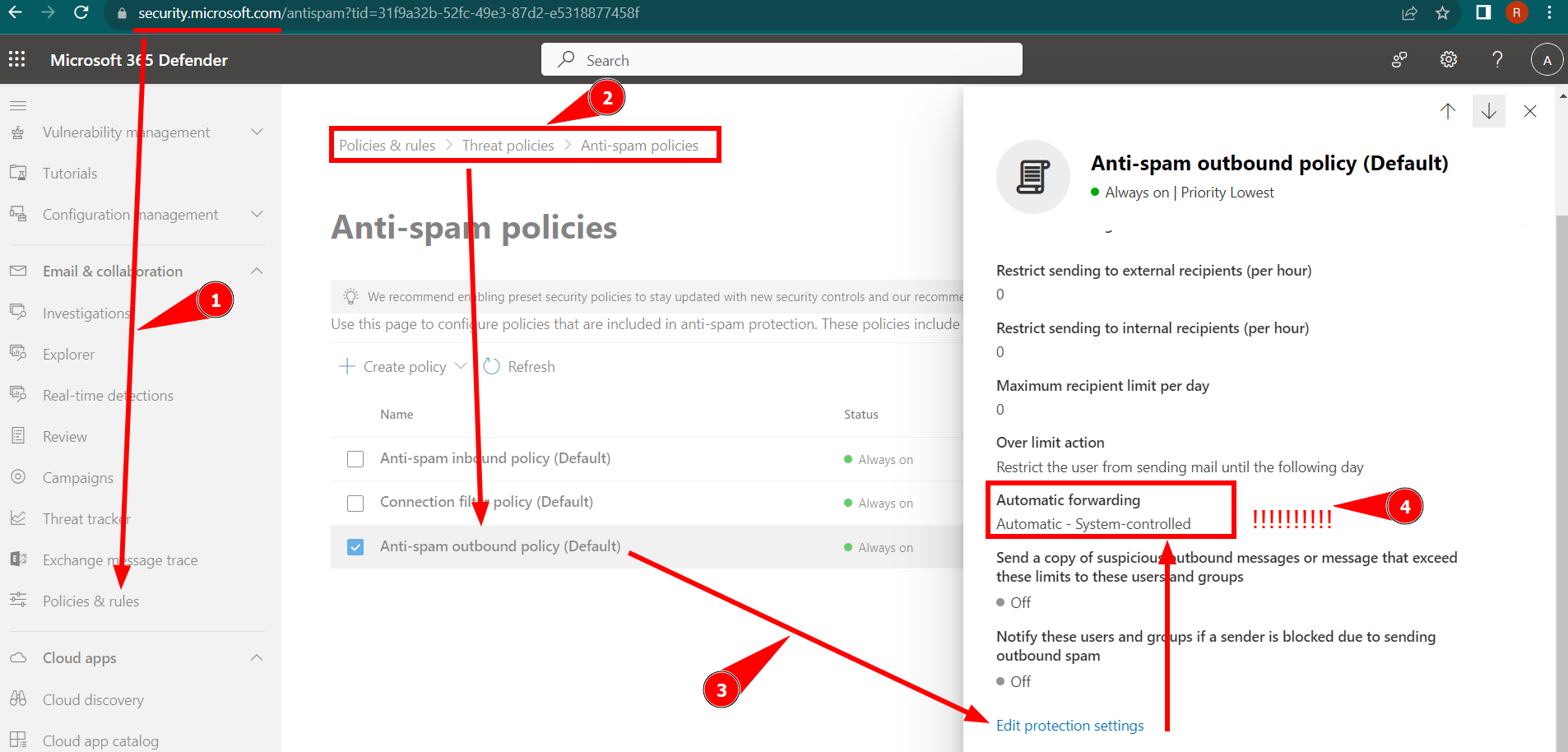
By default it's system controlled which means auto-forwarding will be disallowed. You will have to configure that to allow forwarding, or alternatively you can create a new Anti-Spam Outbound Policy that is scoped to a user, a group, a domain and only allow forwarding on this new policy. Remember, usually the most specific policies take precedence before more general policies in the Microsoft world.
This is also true for the * (star) Remote Domain. You can create a secondary remote domain, say for.. a partner or supplier with which you work often and only allow auto-forwarding to that domain.
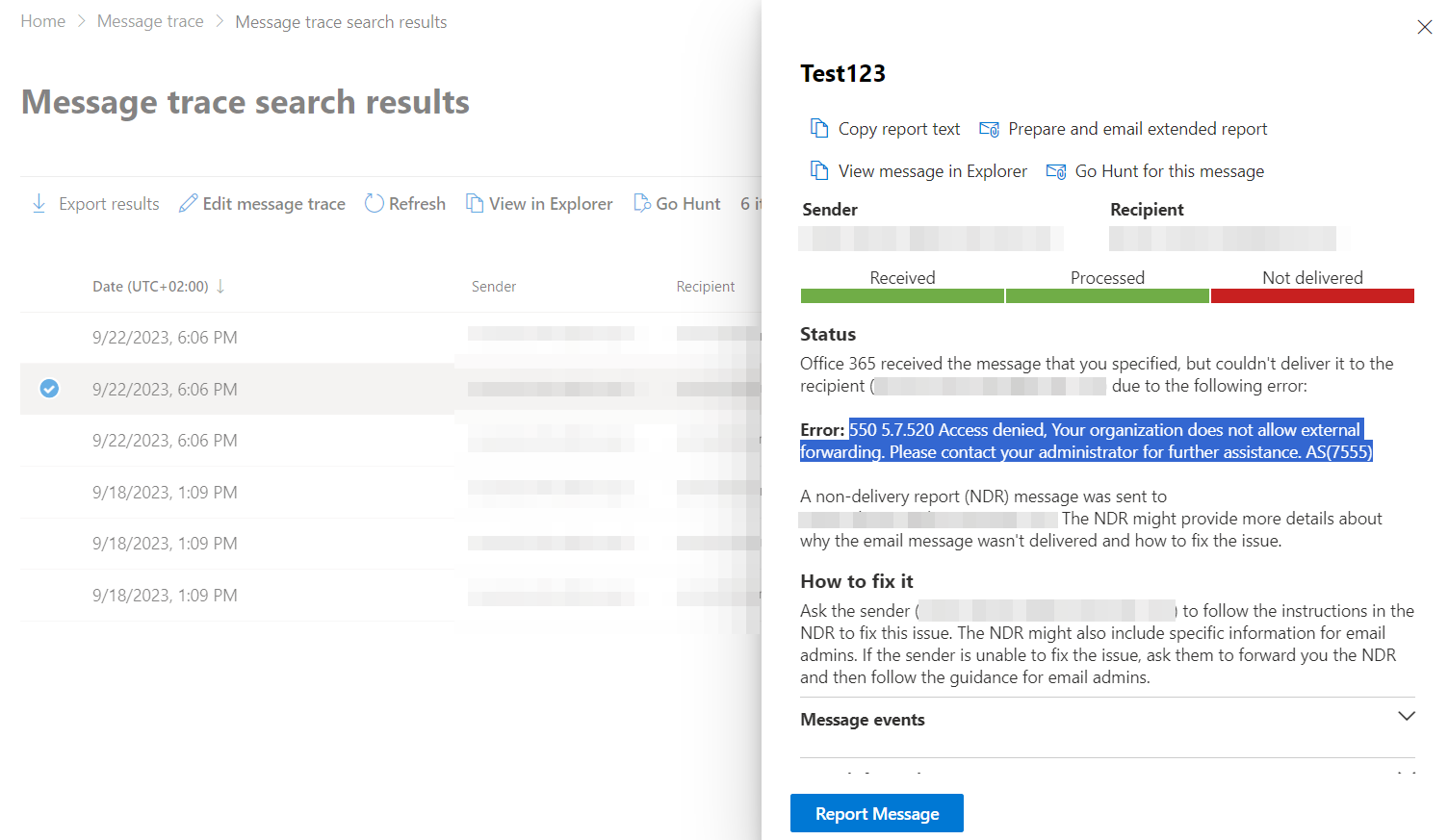
If the Auto-Forwarding is set to System Controlled on the Outbound Anti-Spam Policy, this is the NDR you will receive:
'Remote server returned 550 5.7.520 Access denied, Your organization does not allow external forwarding. Please contact your administrator for further assistance.
Conclusion
This sums up pretty much all of the forwarding scenarios you can have in Exchange Online (most of them also apply to more recent versions of Exchange Server), at user and also tenant level. In this blog post you have all of the needed information to allow or block forwarding for individuals, groups, or an entire domain.
