How to onboard Intune enrolled Windows devices to Defender 🛡️

Introduction
Microsoft Defender for Endpoint is an enterprise security platform that is designed to help organizations detect, prevent and then investigate and respond to advanced threats using a combination of technology built into Windows 10/11 and Microsoft's cloud. 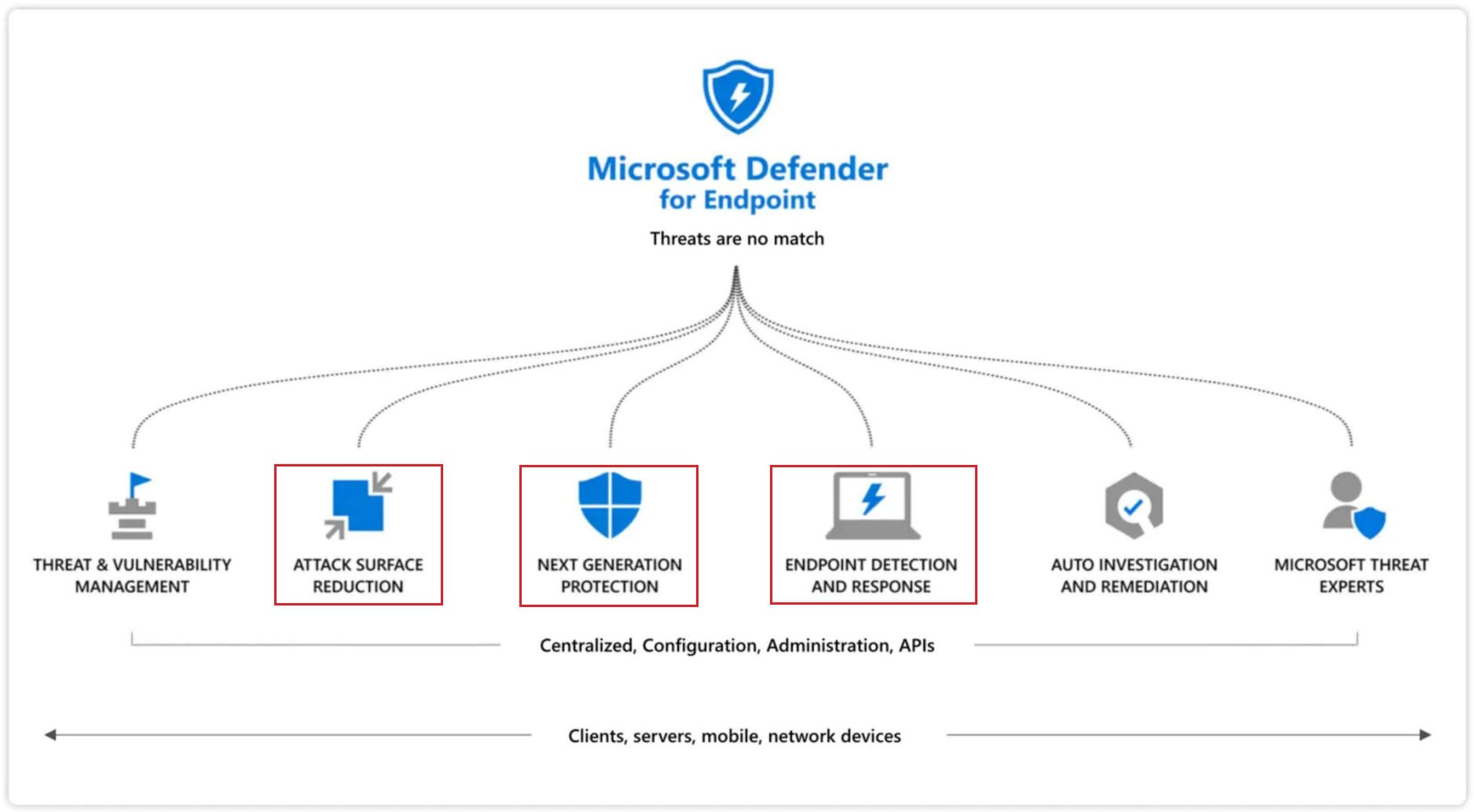
The Benefits of this solution:
- Automated investigation and remediation
- Endpoint Detection and Response (EDR)
- Attack Surface Reduction
- Threat intelligence
- Cloud Security Analytics and much more.
Licensing and PreReqs at the time of writing this article:
-
Defender for Endpoint Plan 1 and Plan 2 (standalone or as part of other Microsoft 365 plans)
-
Microsoft Defender for Business (for small and medium-sized businesses)
-
To onboard servers:
- Microsoft Defender for Servers Plan 1 or Plan 2 (as part of the Defender for Cloud) offering
- Microsoft Defender for Endpoint for Servers
- Microsoft Defender for Business servers (for small and medium-sized businesses only)
-
Data storage: When you run the onboarding wizard for the first time, you must choose where your Microsoft Defender for Endpoint-related information is stored: in the European Union, the United Kingdom, or the United States datacenter.
Turning it on (configuration)
Onboarding Windows 10/11 devices:
-
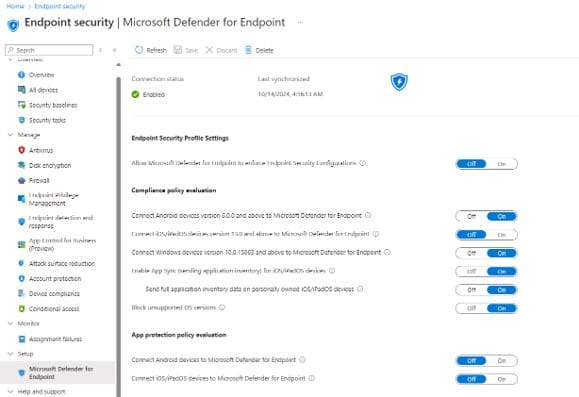
Intune.microsoft.com -> EDR Security -> Turn it on
-
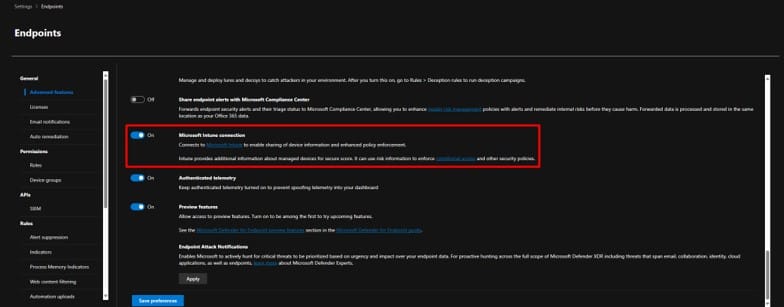
Security.microsoft.com -> Advanced Features -> Microsoft Intune -> On
-
Create an EDR onboarding policy from intune.microsoft.com:
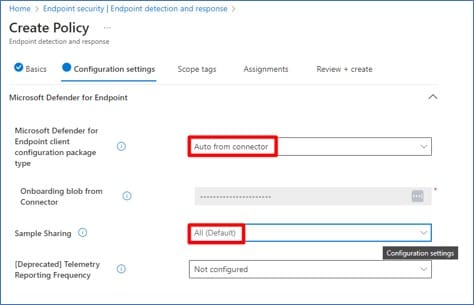
As usual, be sure to test this out on a few devices before going full speed on all company devices.
Defender for servers:
- Plan the deployment (data residency, default workspace or custom Log Analytics, Roles, AWS/GCP automatic enrollment with connector etc)
- Plans comparison (P1 vs P2)
- Deploy the Agent / sensor
- Connect Azure sub / AWS accounts / GCP projects etc.
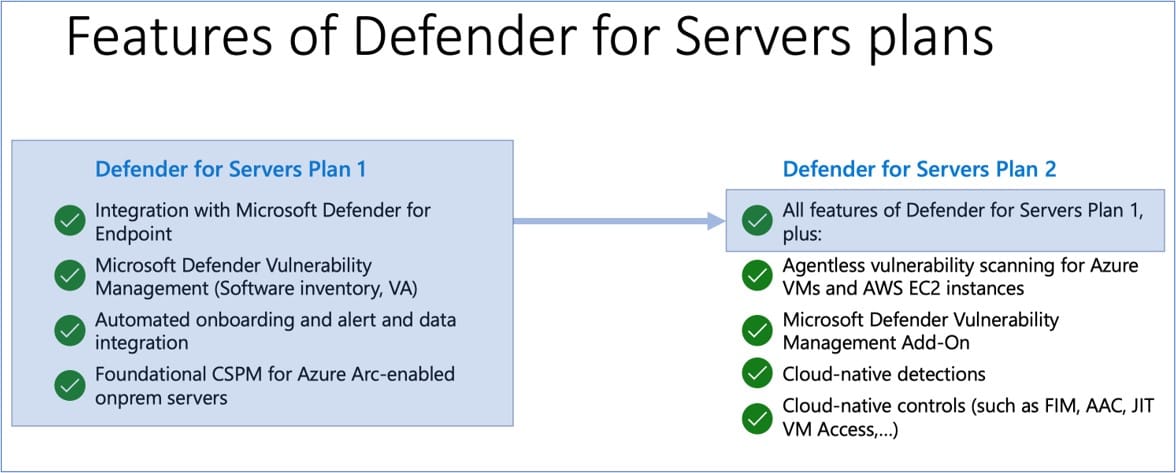
This about covers the onboarding. How to use it and how to configure it is a whole new animal and there are hundreds of settings available, but we'll cover this in another post.
Conclusion
Onboarding devices to Microsoft DEFENDER requires a few steps and configurations, it's not very clear at first sight, but the above steps will guide you to follow the right path.
Special download below 👇
All of the above and much more: links, tips, recommendations and speaker notes organized in a nice PowerPoint presentation are available for you to download, if you sign up/subscribe to this blog. Don't miss out the opportunity to use this presentation with your IT management, if you are an admin; or with your clients, if you are a consultant. All for free!
SUBSCRIBE NOW TO ACCESS THE DOWNLOAD ↓
