Keep Google Chrome Auto-Updating with Intune
Introduction
In the previous post we saw how to deploy Chrome via Intune. Now, what happens is that generally you are pushing a certain app version, and some users might never use it (say they have a preference for Mozilla Firefox or Edge). If they never start/use these apps, in time.. they never get the chance of getting updates, and this causes you to have potential security vulnerabilities. Even more, if your devices are enrolled in Defender for Endpoint, and a Compliance Policy that only accepts devices with a risk score of LOW (or below), then you may start having issues with devices becoming non compliant because of apps that are not updated.
The Fix
We're going to explore WinGet Auto-Update in a future post, and there are certainly multiple solutions to this, but for this specific "Chrome not being up to date" scenario - there's a simple and quick fix that can also serve as an example on how to push a registry key via Intune.
Google has provided us with 2 registry keys which will work in conjunction with Chrome to trigger an auto-update signal that is configurable in minutes:
- HKLM\Software\Policies\Google\Update\ AutoUpdateCheckPeriodMinutes
- HKLM\Software\Policies\Google\Update\ UpdateDefault 1
So the first one regulates the interval (minutes) when the device will check for the updates, and the second one just instructs Chrome to be "open" to accept updates.
NOTE! you can set the first one to 0 (zero) if you want to block Google Chrome from updating. I'm not sure in which scenario you would want that, but if it's your need, it's also possible to configure it from here.
You can try them locally and see the results. I've tested them out and they work. Ok, so now let's get to pushing these through Intune.
Packaging
We can push these 2 as a remediation script, or as a platform script, but I prefer packaging them as a Win32 app, and applying it to a dynamic group (maybe the one containing all the Autopilot devices for example, or the All Users group).
reg add "HKLM\Software\Policies\Google\Update\" /v "AutoUpdateCheckPeriodMinutes" /t REG_DWORD /d 1440 /f
reg add "HKLM\Software\Policies\Google\Update\" /v "UpdateDefault" /t REG_DWORD /d 1 /f
reg add - adds the registry key
1440 - means 24h in minutes
Copy-Paste the above 2 lines in a new file and save it as ChromeRegistry.ps1
Now create a new file, call it UninstallChromeRegistry.ps1 with the following lines:
reg delete "HKLM\Software\Policies\Google\Update\" /v "AutoUpdateCheckPeriodMinutes" /f
reg delete "HKLM\Software\Policies\Google\Update\" /v "UpdateDefault" /f
Next up, we are going to use the Intunewin App Util tool to transform them into an .intunewin file, pointing the installer at the ChromeRegistry.ps1 file.

Hit Enter and you'll have your .intunewin file.
The Deployment
Then moving to Intune, let's create a new App deployment of type Win32:
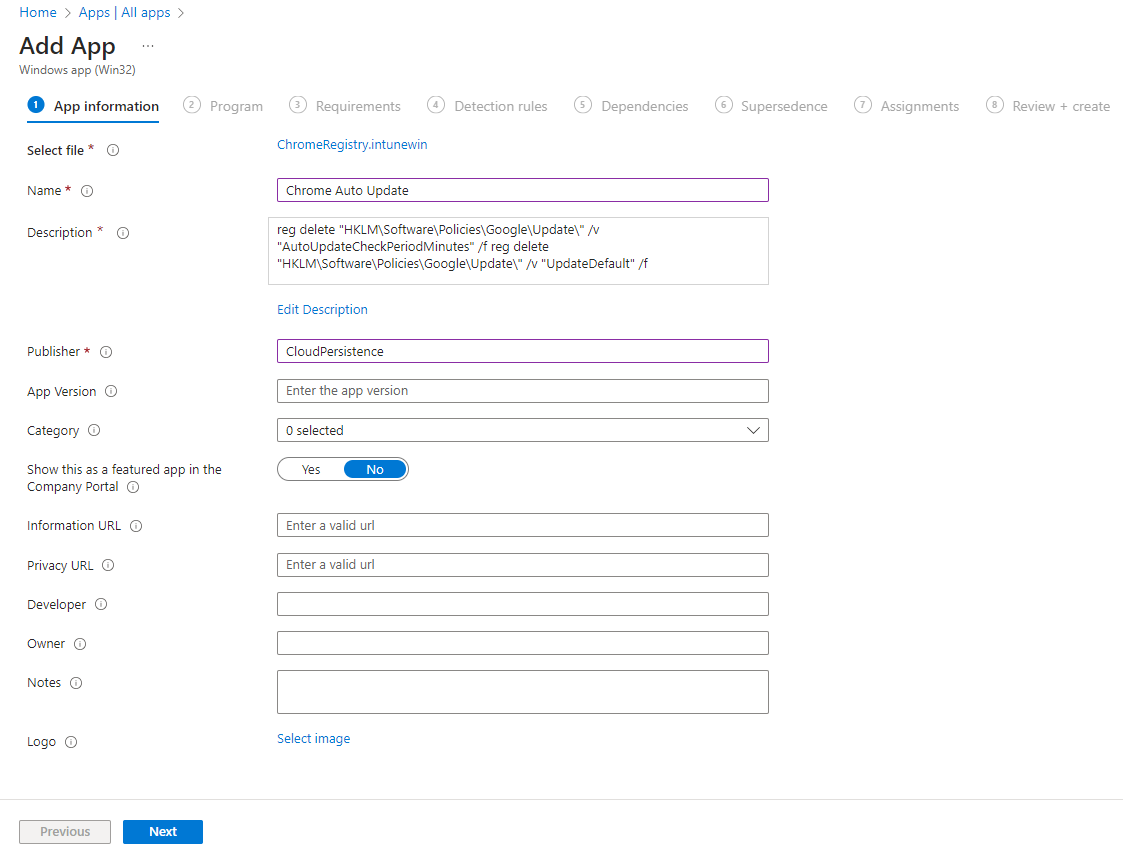
I always prefer putting the script contents in the description, because if you ever lose the original script, it's a real pain to try to intercept and extract it from the .intunewin file.
For the install command, we are going to call PowerShell to run the install script:
%windir%\sysnative\WindowsPowerShell\v1.0\powershell.exe -Executionpolicy Bypass & '.\ChromeRegistry.ps1'
For the uninstall command, we are going to call PowerShell to run the uninstall script:
%windir%\sysnative\WindowsPowerShell\v1.0\powershell.exe -Executionpolicy Bypass & '.\UninstallChromeRegistry.ps1'
For detection rules, we are going to check if one of the registry files exists: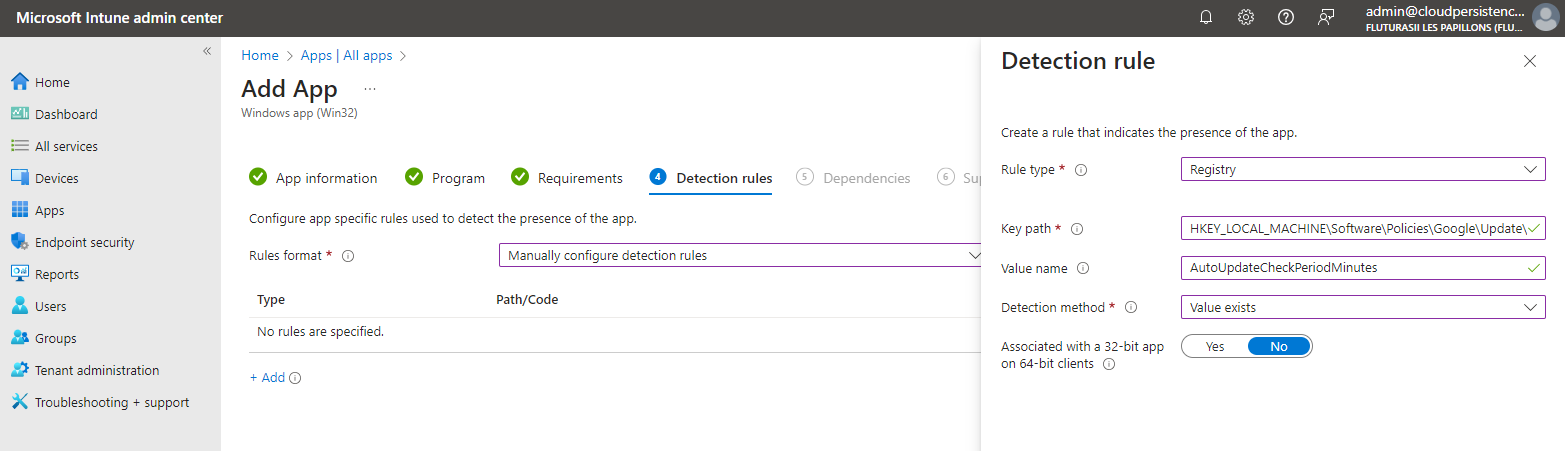
Note! This is a fine example where you could use the Dependency feature to ask Intune to only deploy this "script" if the Chrome app installation also has reported as having been installed. I'm going to cover that separately
Next up, configure your group assignments, Review and Create.
Conclusion
At the next Intune sync, the Registry keys will be deployed on the targeted endpoints, and the Chrome installations will be miraculously always up to date even if not used (opened regularly by the users).
