Manage BitLocker encryption from Intune

Introduction
Hello again, and welcome back! We are going to discuss today about a topic that involves security of data at rest. We already know that data in M365 is encrypted, all of the communication channels are encrypted well via SSL or HTTPS, but what about our physical devices? What if a bad actor steals a device and tries to exfiltrate data directly from the HDD or SDD (storage) of the device? Because afterall.. if he has physical access to the device, he might as well try and do that, right? This means you need to protect data that is at rest, and the best way to do this is to Encrypt the data. Bitlocker can help us achieve this.
Configure Bitlocker
Prerequisites
- Device must be Entra Joined or Microsoft Entra Hybrid Joined
- TPM 2.0 preferred (min 1.2)
- BIOS set to UEFI
- Win 10 1809 or 11
- Not have any other 3rd party encryption enabled
- You will need permissions in Intune in order to configure this
How to configure
There are multiple ways to achieve this, but I am assuming the following:
- Your users are Standard Users (not Administrators on the device)
- You want to enable this silently so they don't have prompts
In order to deploy it silently, you will need to configure the next settings as follows:
- Hide prompt about third-party encryption = Yes
- Allow standard users to enable encryption during Autopilot = Yes
- Require Key File Creation = Allowed or Blocked
- Recovery Password Creation = Allowed or Required
Go to Intune.Microsoft.com and from here you have 2 ways of creating this policy:
- From Endpoint Security -> Disk Encryption -> Create New
- From Devices -> Configuration Profiles -> Endpoint Security -> Windows Encryption
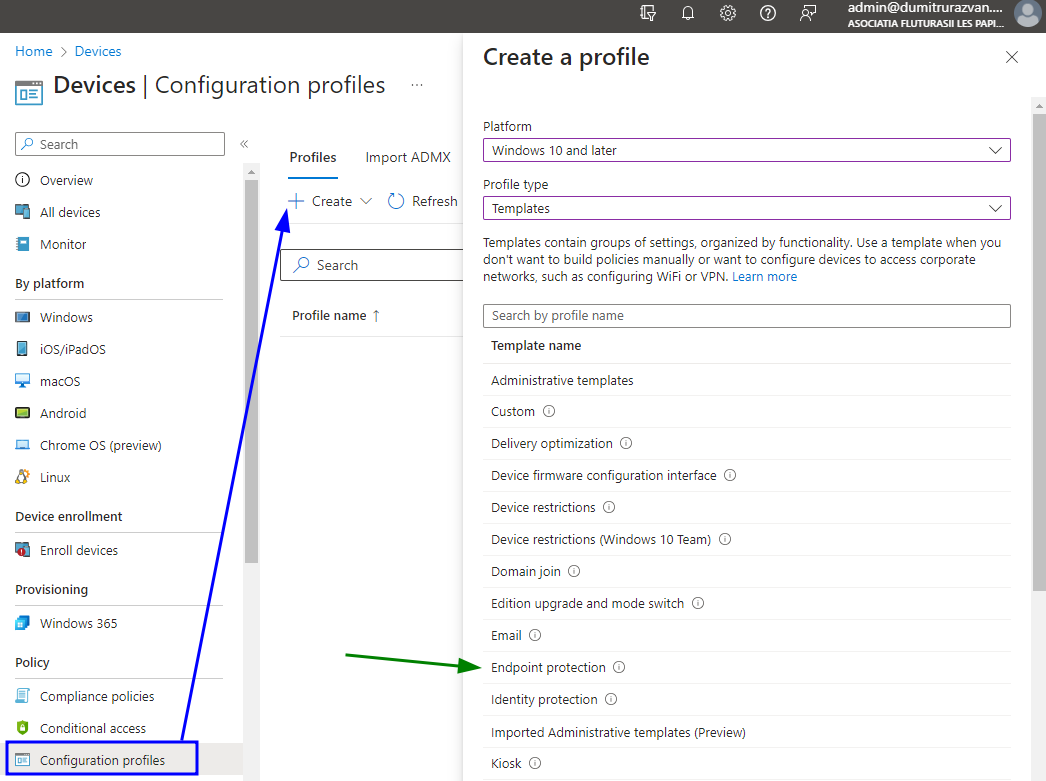
I would reccomend you go with the 2nd option. There, I would reccomend you configure the following:
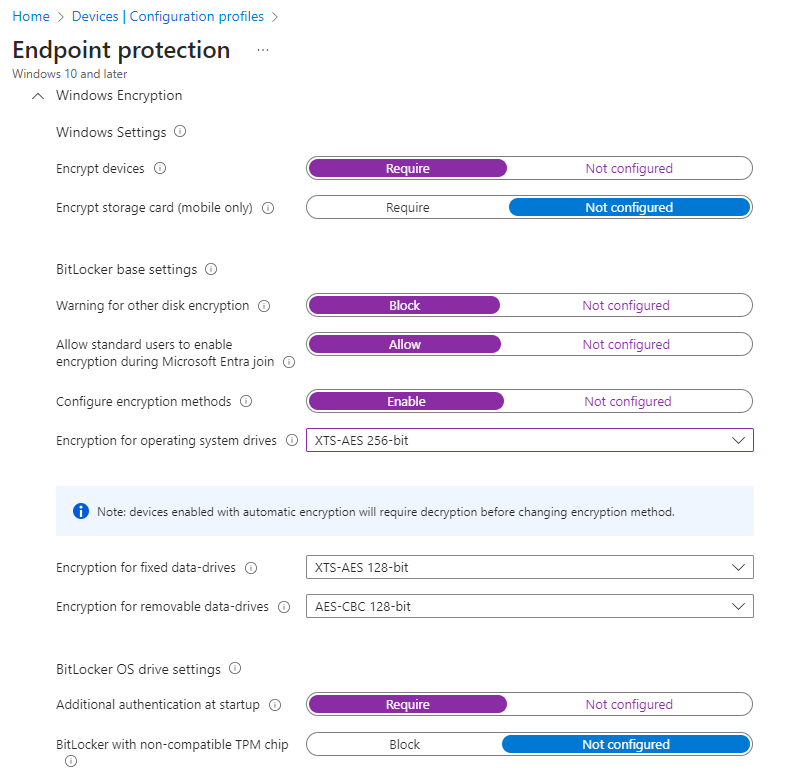
You can of course change the settings to your needs. I have configured the maximum encryption complexity of 256 bits.
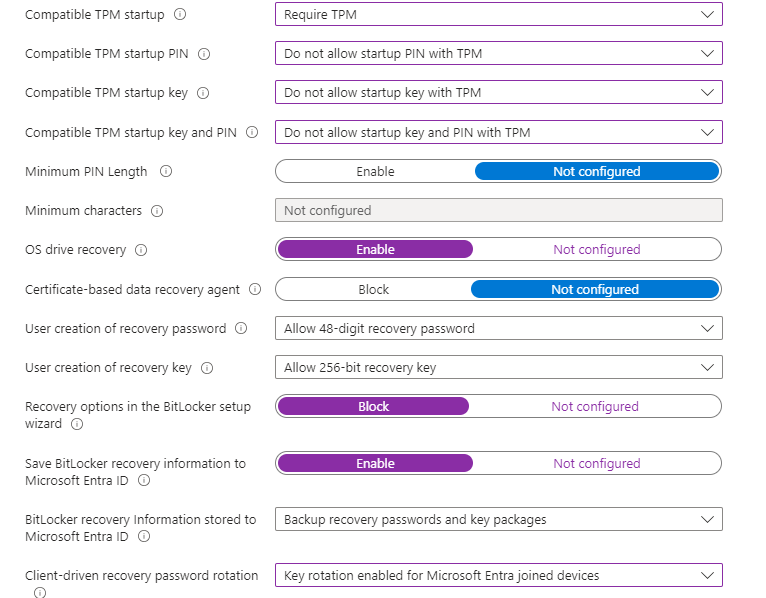
Very important here to enable saving the recovery key in Entra (Azure) so that you can unblock users that get locked out just by fetching the key from Entra.
The rest I left as default.
For more details, I would reccomend you check the official doc. Last but not least, I urge you test this out properly before deploying it to all users. Don't just take my word for it as behaviors and settings can change in the meantime and they can yield different results.
Conclusion
Encrypting drives is a very good security practice that you can use to protect your endpoint's physical drives. This can be easily achieved via Intune, and it can work in tandem with Autopilot, starting the encryption with the start of the Out of the box experience. Hope this helps to elevate your security score in your organization.
