Secure your newly bought email domain (SPF, DKIM, DMARC)

Introduction:
Buying a new domain is always a cheerful moment. Be it because you have a merger, an acquisition, or you're just going through a change of business names, or trying out new things. Whatever the reason, getting a new domain is always refreshing and exciting. What's not so exciting is having to configure it for use with your M365 tenant. Well.. in this post we'll try to make it an extremely easy task.
SPF, DKIM, DMARC(background):
- An email authentication technique called Sender Policy Framework (SPF) makes it possible to determine the mail servers that a specific domain has granted permission to deliver email. ISPs can identify phishers, scammers, and spoofers who attempt to send malicious email using a domain that is associated with a business or brand by utilizing SPF.
- DomainKeys Identified Mail, or DKIM, is a technique for email authentication that makes use of a digital signature to inform the recipient of an email that the message was sent and approved by the owner of a domain.
- Email authentication, reporting, and conformance are all part of the DMARC protocol, which stands for "Domain-based Message Authentication, Reporting & Conformance". It improves and monitors security of the domain from fraudulent email by linking to the author's ("From:") domain name, publishing policies for recipient treatment of authentication failures, and reporting from receivers to senders. It builds on the widely used SPF and DKIM protocols.
Ok, Ok, give me the exact records:
a) SPF - i've included an additional service you might have to include (service.domain.name) which can be anything else you might be using in your organization to authorize sending from your tenant. So please replace that with your actual 3rd party service, or take it out of the record if you don't have any extra such service (ticketing app, printers, 3rd party marketing apps etc.)
Note! - be mindful of the 10 SPF lookup limit. If you need to add more than 10 services to your SPF (to allow those services to send as your domain), you will need to do some “SPF Flattening”. There are online tools offering such capabilities (Dmarcly, AutoSPF, PowerDMARC etc.). Also, the best 3rd party tool to check how many SPF lookups your SPF record is using is: https://dmarcian.com/spf-survey/
| Record Name | Type | Pointer | Data | TTL |
|---|---|---|---|---|
| SPF | TXT | @ | v=spf1 include:spf.protection.outlook.com include:service.domain.name -all | 3600 |
b) DKIM - you first need to turn it on (it will fail at first), create the records, then enable it:
connect-exchangeonline
New-DkimSigningConfig -DomainName “yournewdomain.com” -Enabled $true
Then create these records:
| Record Name | Type | Pointer | Data | TTL |
|---|---|---|---|---|
| DKIM1 | CNAME | selector1._domainkey | selector1-dom-ain._domainkey.domain.onmicrosoft.com | 3600 |
| DKIM2 | CNAME | selector2._domainkey | selector2-dom-ain._domainkey.domain.onmicrosoft.com | 3600 |
Now you might be wondering how do you find out those exact values. Well, there's a simple way either from the GUI (compliance.microsoft.com -> Policies and you track down the DKIM page), or from the above cmdlet which will give you the exact values:
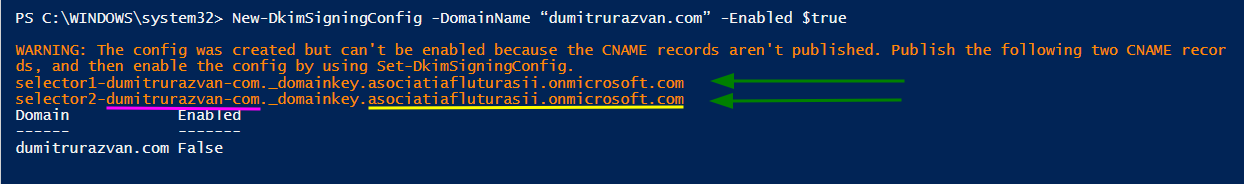
I've outlined with magenta the part of the info that represents the new domain, and with yellow the part that comes from the tenant associated with the initial onmicrosoft domain. That's how you can doublecheck if your record is well built.
Once the records are in place, don't forget to ENABLE them from the tenant either by powershell or from the GUI.
c) DMARC
| Record Name | Type | Pointer | Data | TTL |
|---|---|---|---|---|
| DMARC | TXT | _dmarc | v=DMARC1; p=none; ruf=mailto:dmarc@yourdomain.com;fo=0; | 3600 |
NOTE! The mailto address is a fictional one. You can indeed get all those reports delivered back to you in something like a shared mailbox, but most people go out and buy a 3rd party service that can generate some nice charts and reporting out of all of those reports.
Also, to be noted that both SPF and DMARC have a ton of options to customize. It's not in the scope of this article, but you can choose what happens to emails that fail those tests such as hard fail, soft fail and other concepts that these DNS protection methods have.
Finally, time to test your work! For this, my advice would be to use any number of free-to-use online SPF, DMARC, DKIM records checker. (MXToolbox, or easydmarc, dmarcian etc.)
Conclusion:
Securing your newly bought email domain name isn't that difficult. You just have to setup your SPF, DKIM and DMARC. Most people barely set up their SPF, so doing all 3 would put you at a great advantage.
