Stop and find out: Why you need Conditional Access Policies
Introduction
Conditional Access Policies in Azure are typically one of the first layers of security that a tenant will have as they control who signs in, from where, to what, using what IP/Location etc. Defining a good set of CAs can set you way ahead in securing your O365 cloud services and data. Other benefits include:
- providing your users with secure access
- allowing you to reach certain compliance levels and meeting security standards
- giving you (as an admin) much more control over who and what connects into your tenant
Configuration
I'll showcase a few typical CAs, but an important note here is that there's no one size fits all. CAs are really customizable and each business might have a different scenario that needs a different configuration. In your organization you better consult with the Security Architect, or you can reach out to us for designing a set of multiple CA policies to cover the basics (generally somewhere between 5-10 CAs is a good start).
CA01 - Require All users to input MFA every 24h
Today we're going to talk about the 24h MFA one. The purpose of this CA Policy is.. as its name suggests.. very clear. 24h may seem too strict for you, or too annoying for the user, but maybe it's too loose for a bank which might want to configure that to 12h or even 8h. (See.. as I was saying, CAs are realy not one size fits all).
We are going to navigate to https://portal.azure.com/#view/Microsoft_AAD_ConditionalAccess/ConditionalAccessBlade/~/Policies to create a new Policy, give it a name then select to which users this applies to:
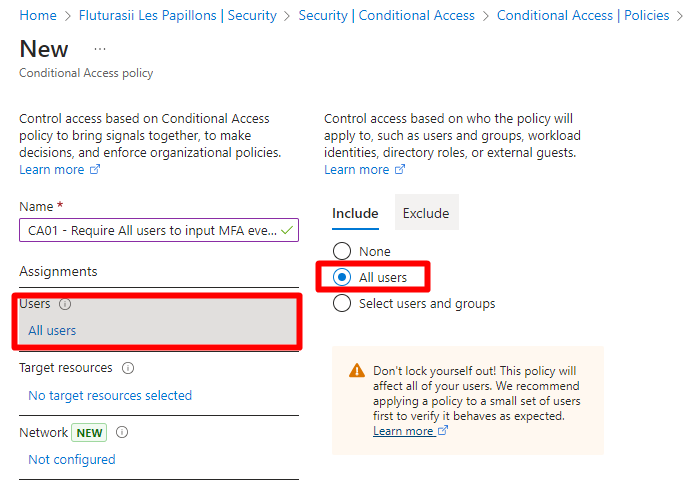
This can obviously be scoped at a certain group of users or guests - for example, maybe you would like only externals or sales reps that are daily on the field to have this extra-security measure imposed, and a more relaxed CA policy for users that come into the office daily.
After that, exceptions:
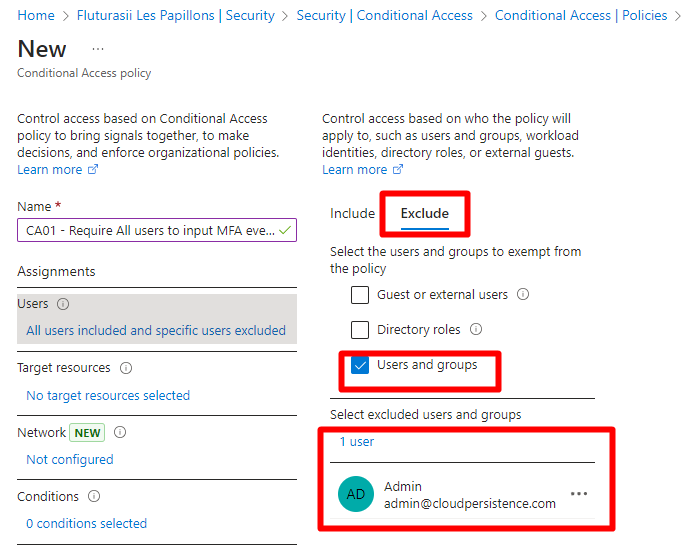
NOTE!!! Define a break the glass account/ice-breaker in your organization. This account typically has permanent Global Admin Permissions and its password is very secure (+24char), no MFA, and is kept secret, only accessible by 1-2 key admins/IT Managers. Then, exclude this ice-breaker account from all CA policies to protect yourself from ever locking up the tenant accidentally. In my test lab I'll use the admin account
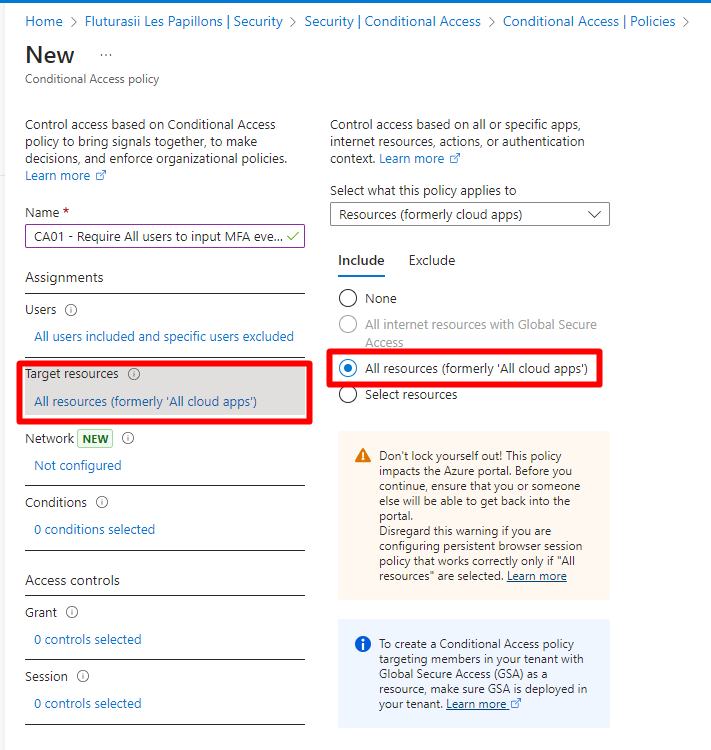
Next up, I'll configure this CA policy to apply on All Cloud Apps:
When accessed via a Browser:
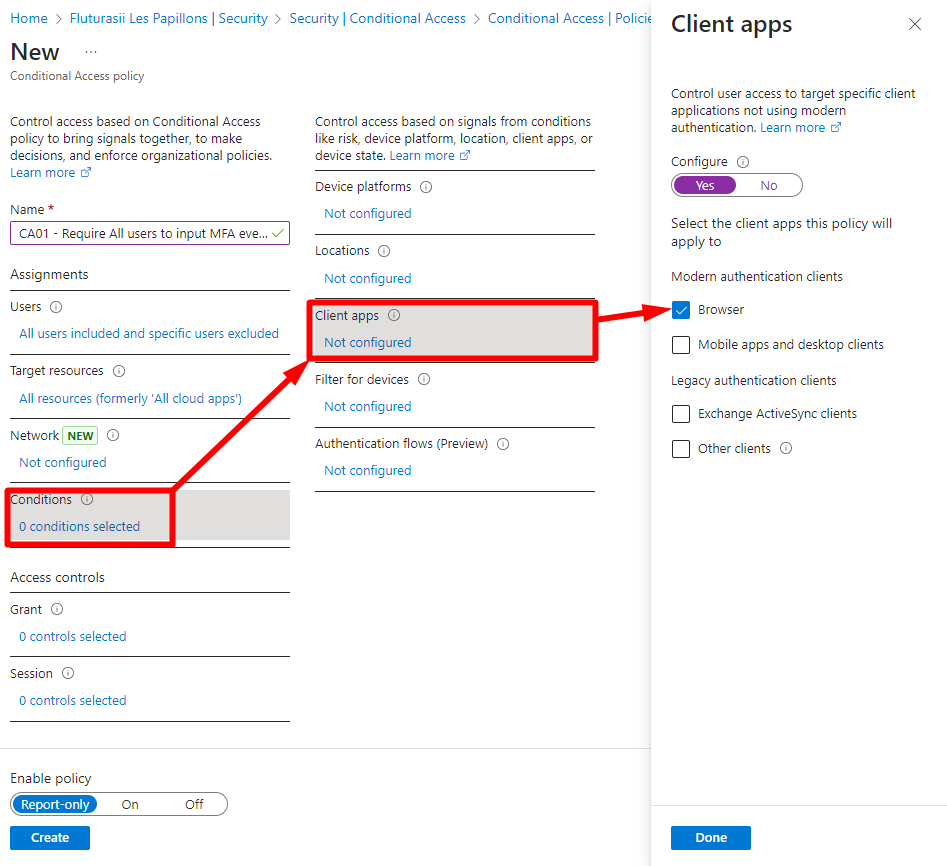
And I'll require MFA:
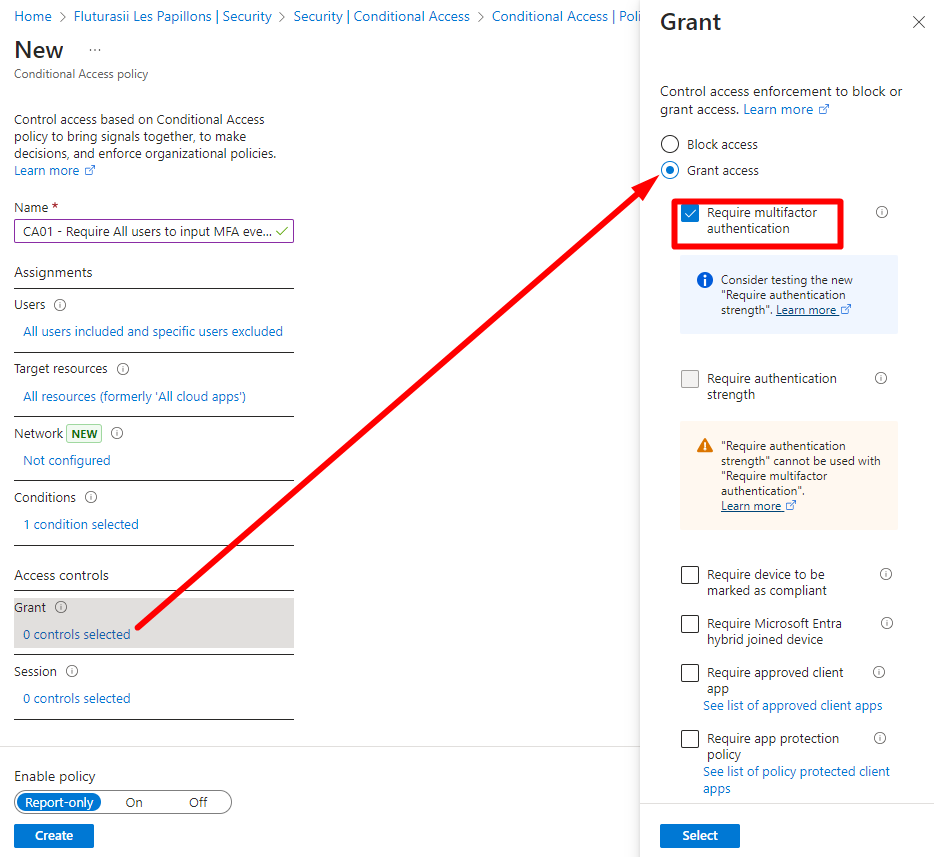
Just remember here that you can also require users to connect from a device that is registered, or marked as compliant, or all together. In my specific scenario I'm really looking to force MFA/24h for everyone, so I won't tick anything else:

Sign in frequency - 1 day:
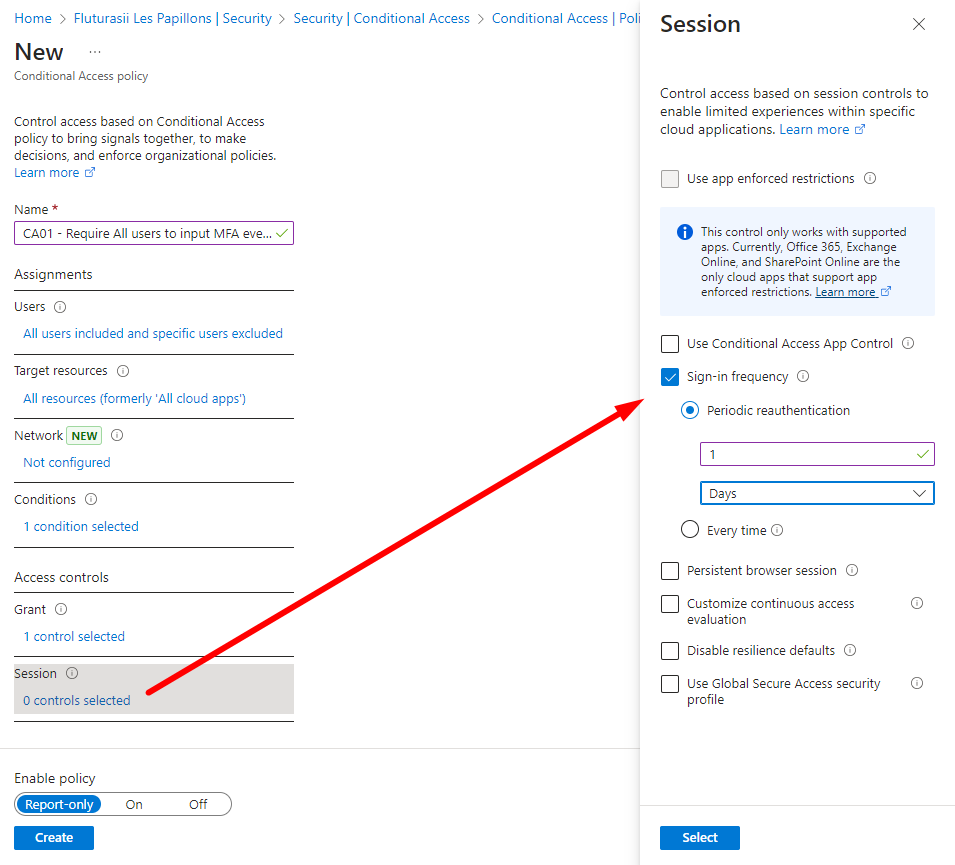
And don't forget to leave the CA Policy on Report-Only at least for a few days in order to evaluate if the CA has a potential risk of blocking legitimate connections or causing other damage:
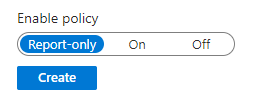
I'm going to showcase in a follow-up post how to evaluate CA's potential outcome with the What IF tool and with the Insights tool.
Conclusion
CA Policies can help secure your connections and your user's sessions. To input MFA every 24h can be a bit irritating for the users, but can also be a great security measure, because you basically protect any session from unwanted access after the 24h mark. Please reach out using the About page if you need more guidance on this, or if you have questions. Be sure to register/subscribe for future premium content and guides.
